Profiles and Namespaces
What is a Kubeflow Profile?
A Kubeflow Profile is a Kubernetes CRD introduced by Kubeflow that wraps a Kubernetes Namespace. Profiles are owned by a single user, and can have multiple contributors with view or modify access. The owner of a profile can add and remove contributors (this can also be done by the cluster administrator).
Profiles and their child Namespaces are reconciled by the Kubeflow Profile Controller and contributors (not owners) are managed by the Kubeflow Access Management API (KFAM).
Profiles in the Central Dashboard
Select the active profile with the drop-down found in the top bar of Kubeflow Central Dashboard. Most Kubeflow components use the active profile to determine which resources to display, and what permissions to grant.
Users can only see profiles to which they have owner, contributor (read + write), or viewer (read) access.
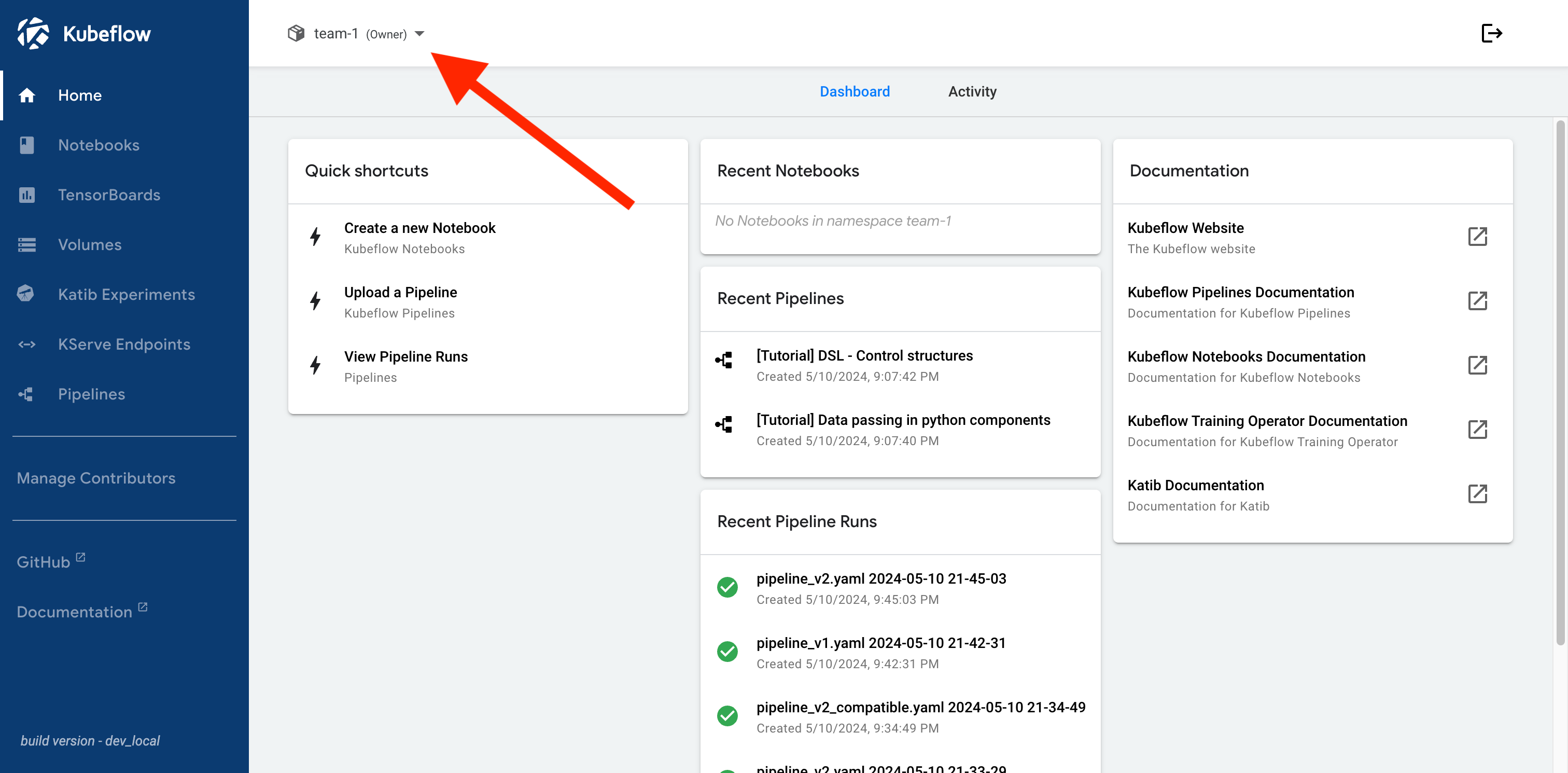
Automatic Profile Creation
Kubeflow supports automatic profile creation for users who log into Kubeflow for the first time.
The CD_REGISTRATION_FLOW environment variable on the central-dashboard Deployment controls whether automatic profile creation is enabled.
By default, automatic profile creation is disabled.
When CD_REGISTRATION_FLOW is true, if a user logs into Kubeflow, and is not already a profile owner, they will be prompted to create a profile.
Warning
Automatic profile creation may not be suitable for all use cases.
Users become owners of the automatically created profile, so can add/remove contributors.
Cluster administrators may choose to disable automatic profile creation and manually create profiles for users and/or teams. Typically, in these cases, users are only given view or modify access to profiles (not made owners).
Here is an example of the automatic profile creation flow:
- A new user logs into Kubeflow for the first time:

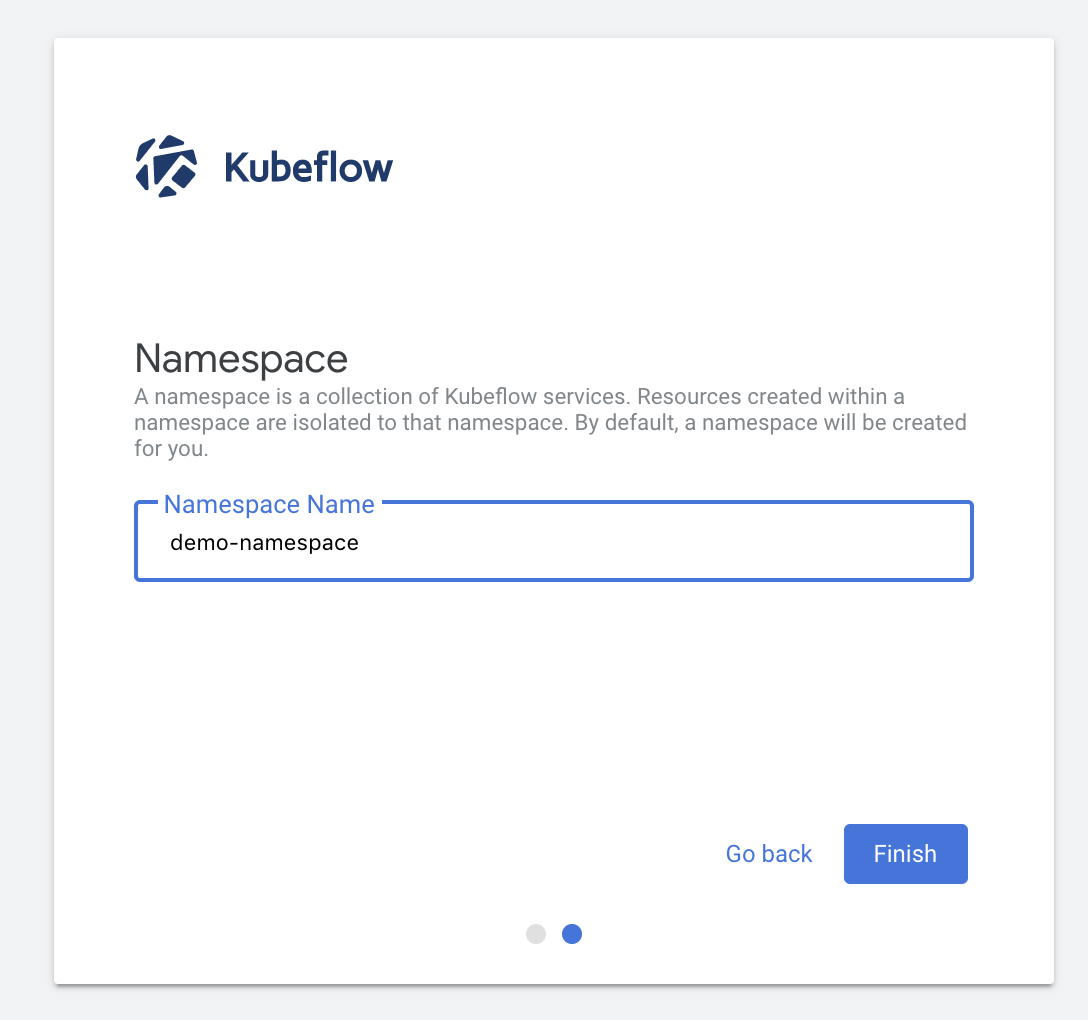
- The user can name their profile and click Finish:
Profile Resources
The following resources are created for each profile:
- A Kubernetes Namespace that shares the same name as the profile.
- Kubernetes RBAC for Users:
- For profile owner, a
RoleBindingnamednamespaceAdmintoClusterRole/kubeflow-admin - For each contributor, a
RoleBindingnameduser-{EMAIL}-clusterrole-{ROLE}toClusterRole/kubeflow-{ROLE}{EMAIL}is the email of the contributor, special characters replaced with-, cast to lowercase.{ROLE}is the role of the contributor, eithereditorview
- For profile owner, a
- Kubernetes RBAC for ServiceAccounts:
- For
ServiceAcount/default-editor, aRoleBindingnameddefault-editortoClusterRole/kubeflow-edit - For
ServiceAcount/default-viewer, aRoleBindingnameddefault-viewertoClusterRole/kubeflow-view
- For
- Istio AuthorizationPolicies:
- For the profile owner, an
AuthorizationPolicynamedns-owner-access-istio - For each contributor, an
AuthorizationPolicynameduser-{EMAIL}-clusterrole-{ROLE}{EMAIL}is the email of the contributor, special characters replaced with-, cast to lowercase{ROLE}is the role of the contributor, eithereditorview
- For the profile owner, an
Manage Profiles
Because a Profile is a Kubernetes CRD, a cluster administrator can use kubectl commands to manage profiles.
Create a Profile
A cluster administrator can create a new profile with kubectl commands.
First, create a file named my-profile.yaml with the following structure:
apiVersion: kubeflow.org/v1
kind: Profile
metadata:
## the profile name will be the namespace name
## WARNING: unexpected behavior may occur if the namespace already exists
name: my-profile
spec:
## the owner of the profile
## NOTE: you may wish to make a global super-admin the owner of all profiles
## and only give end-users view or modify access to profiles to prevent
## them from adding/removing contributors
owner:
kind: User
name: admin@example.com
## plugins extend the functionality of the profile
## https://github.com/kubeflow/kubeflow/tree/master/components/profile-controller#plugins
plugins: []
## optionally create a ResourceQuota for the profile
## https://github.com/kubeflow/kubeflow/tree/master/components/profile-controller#resourcequotaspec
## https://kubernetes.io/docs/reference/kubernetes-api/policy-resources/resource-quota-v1/#ResourceQuotaSpec
resourceQuotaSpec: {}
Next, run the following command to create the profile:
kubectl apply -f my-profile.yaml
List all Profiles
A cluster administrator can list existing profiles using the following command:
kubectl get profiles
Describe a Profile
A cluster administrator can describe a specific profile using the following command:
kubectl describe profile MY_PROFILE_NAME
Delete a Profile
A cluster administrator can delete an existing profile using the following command:
kubectl delete profile MY_PROFILE_NAME
Warning
Deleting a profile also deletes the corresponding Namespace from the cluster.All resources created in the profile namespace will be deleted.
Manage Profile Contributors
Profile contributors are defined by the presence of specific RoleBinding and AuthorizationPolicy resources in the profile namespace.
Note
The central dashboard method ONLY allows you to add contributors with “edit” access.To add contributors with “view” access, you must use the manual method.
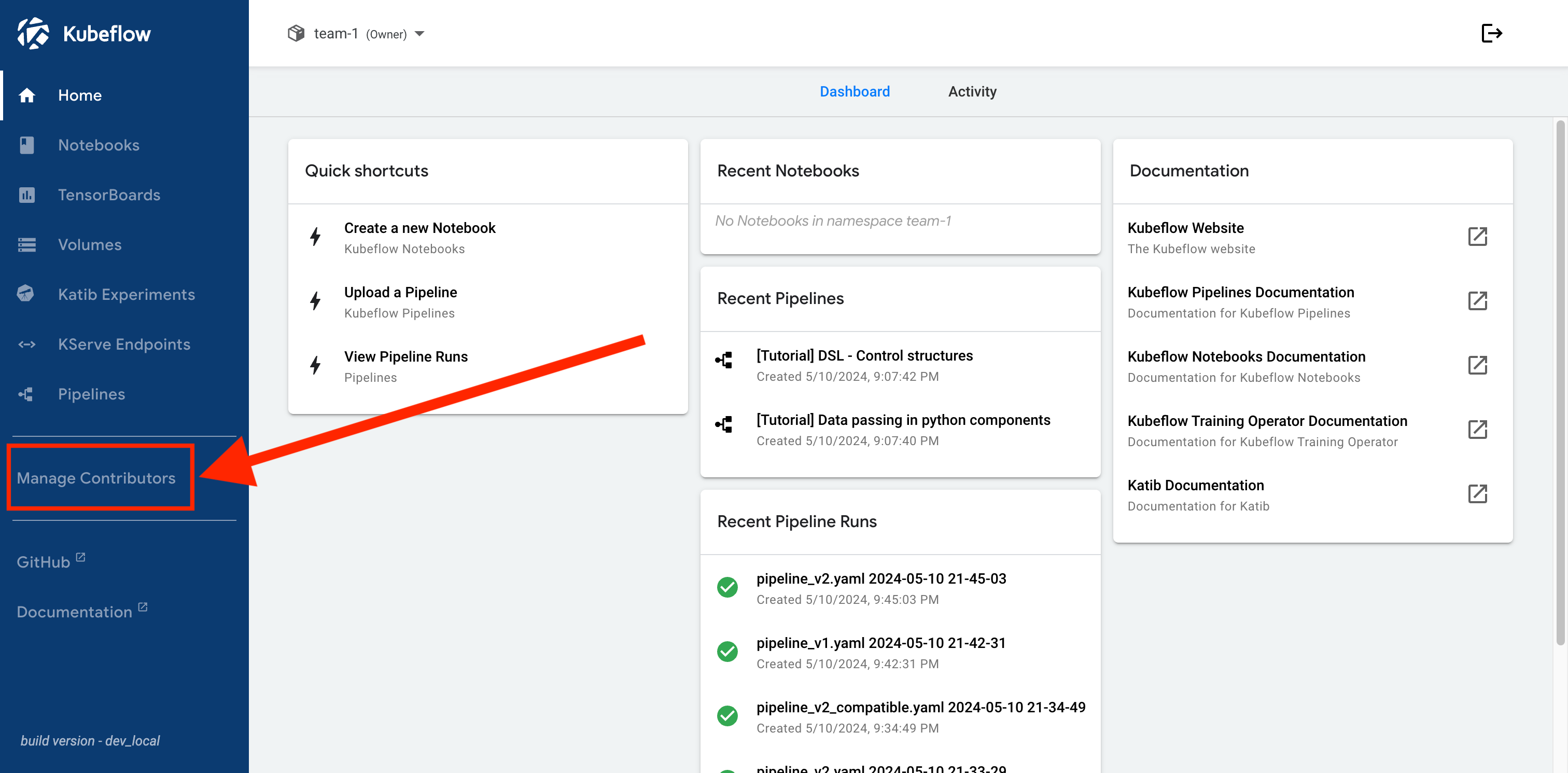
Manage Contributors with Central Dashboard
The owner of a profile can use the Manage Contributors tab in the Kubeflow Central Dashboard to add or remove contributors.
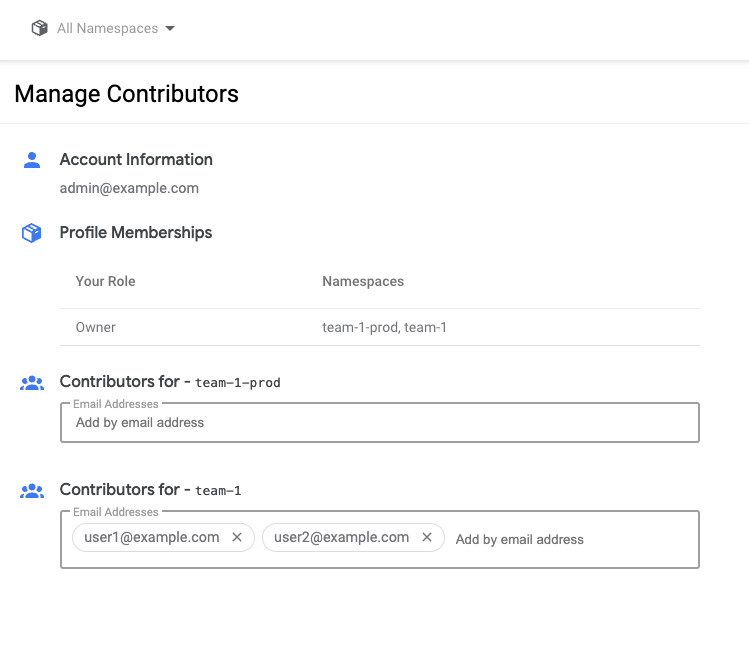
Contributors are managed with the “Contributors to your namespace” field.
Manage Contributors Manually
An administrator can manually add contributors to an existing profile by creating the required RoleBinding and AuthorizationPolicy resources in the profile namespace.
Create Contributor RoleBinding
The RoleBinding which grants a user access to a profile is structured as follows:
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: user-<SAFE_USER_EMAIL>-clusterrole-<USER_ROLE>
namespace: <PROFILE_NAME>
annotations:
role: <USER_ROLE>
user: <RAW_USER_EMAIL>
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: kubeflow-<USER_ROLE>
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: <RAW_USER_EMAIL>
Where the following variables are replaced with the appropriate values:
<RAW_USER_EMAIL>the email of the user (case-sensitive)<SAFE_USER_EMAIL>the email of the user (special characters replaced with-, and cast to lowercase)<USER_ROLE>the role of the user, eithereditorview<PROFILE_NAME>the name of the profile
Create Contributor AuthorizationPolicy
The AuthorizationPolicy which grants a user access to a profile is structured as follows:
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: user-<SAFE_USER_EMAIL>-clusterrole-<USER_ROLE>
namespace: <PROFILE_NAME>
annotations:
role: <USER_ROLE>
user: <RAW_USER_EMAIL>
spec:
rules:
- from:
- source:
## for more information see the KFAM code:
## https://github.com/kubeflow/kubeflow/blob/v1.8.0/components/access-management/kfam/bindings.go#L79-L110
principals:
## required for kubeflow notebooks
## TEMPLATE: "cluster.local/ns/<ISTIO_GATEWAY_NAMESPACE>/sa/<ISTIO_GATEWAY_SERVICE_ACCOUNT>"
- "cluster.local/ns/istio-system/sa/istio-ingressgateway-service-account"
## required for kubeflow pipelines
## TEMPLATE: "cluster.local/ns/<KUBEFLOW_NAMESPACE>/sa/<KFP_UI_SERVICE_ACCOUNT>"
- "cluster.local/ns/kubeflow/sa/ml-pipeline-ui"
when:
- key: request.headers[kubeflow-userid]
values:
- <RAW_USER_EMAIL>
Where the following variables are replaced with the appropriate values:
<RAW_USER_EMAIL>the email of the user (case-sensitive)<SAFE_USER_EMAIL>the email of the user (special characters replaced with-, and cast to lowercase)<USER_ROLE>the role of the user, eithereditorview<PROFILE_NAME>the name of the profile<KUBEFLOW_NAMESPACE>the namespace where Kubeflow is installed<KFP_UI_SERVICE_ACCOUNT>the name of the ServiceAccount used byml-pipeline-uiPod<ISTIO_GATEWAY_NAMESPACE>the namespace containing the Istio Gateway Deployment<ISTIO_GATEWAY_SERVICE_ACCOUNT>the name of the ServiceAccount used by the Istio Gateway Pods
Feedback
Was this page helpful?
Thank you for your feedback!
We're sorry this page wasn't helpful. If you have a moment, please share your feedback so we can improve.